Hi, I decided to write this tutorial because of a request. This time, we won’t use windbg, or any other debugger. I’ll make another tutorial for this approach.
So Target : http://ge.tt/7b0Shli2
First, we have to decrypt the methods. Go to module -> .cctor and place a breakpoint just after the first call :
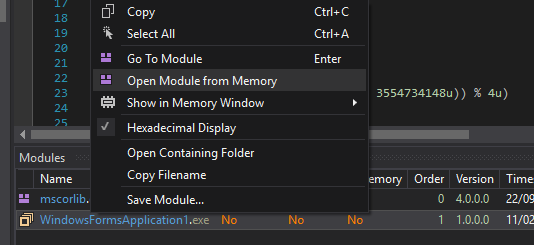
Debug the exe and open module (Ctrl + Alt + u) :
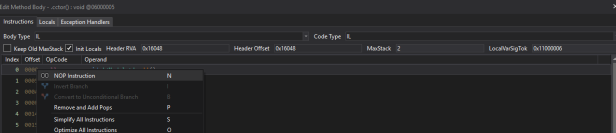
Go again in module -> .cctor and nop the two first calls :
Methods are now decrypted. We had to remove this call because this call will decrypt the methods and methods are decrypted. Now save the module using this options :
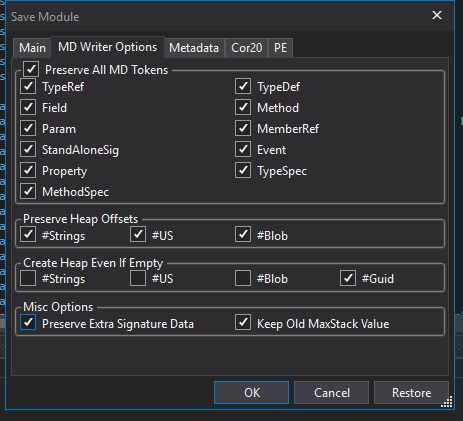
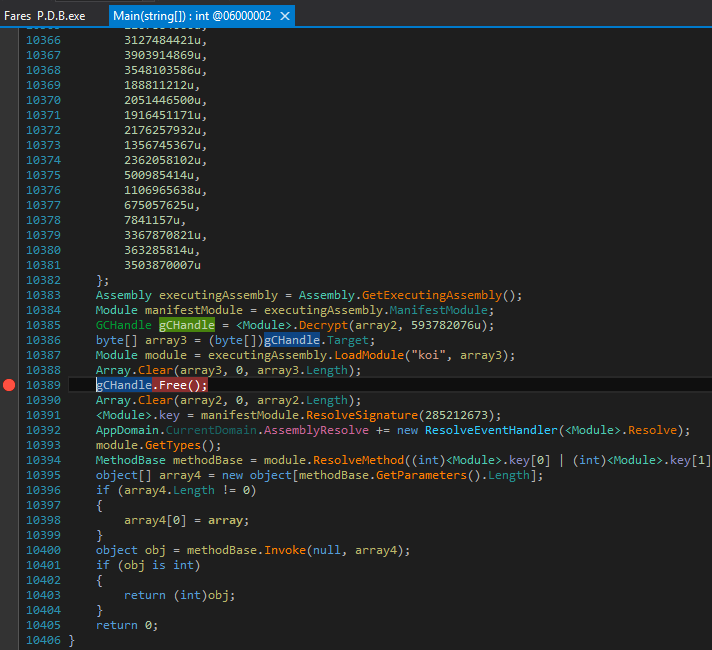
Now we have to remove the Packer. For that, we need dnSpy debugger. Go to the entry point and scroll to the bottom. Place a breakpoint on GCHandle.Free();
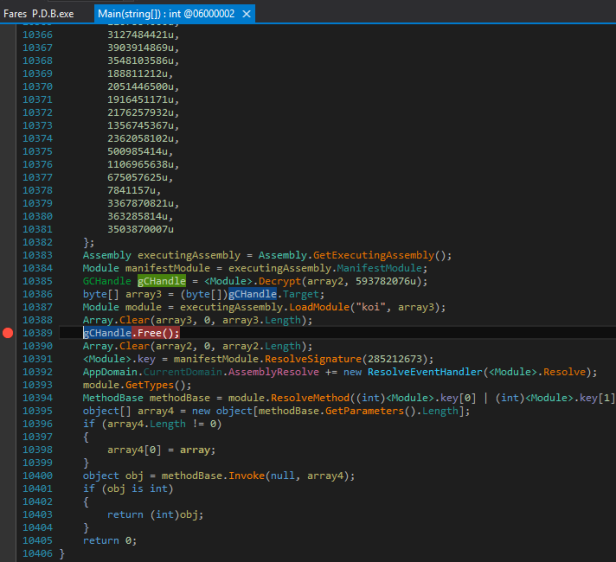
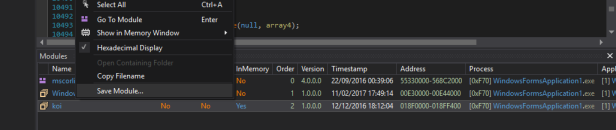
Then start the debug and wait for the breakpoint. When it hit, open modules (Ctrl + Alt + u)
And save the decrypted module that is called koi !
If you try to run the exe, it won’t start because we have to fix the entry point.
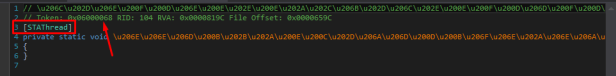
Look for the method that has [STAThread], it’s the entrypoint, copy the Token and open the exe in CFF Explorer. Modify the entry point token with the token of this method.
Now load the exe fixed in dnspy. Go again in module -> .cctor and place a breakpoint after the call. The, a second time, save the module
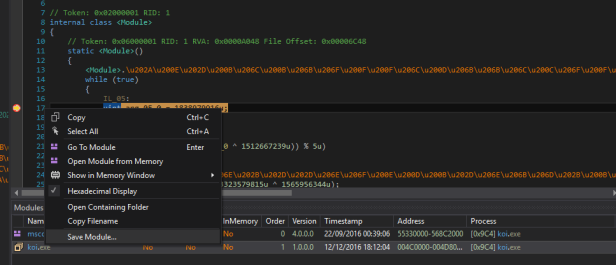
Fix the entry point a second time … Attention : when you save the exe, don’t forget the option that i mentionned before.
Now the exe should be runable !
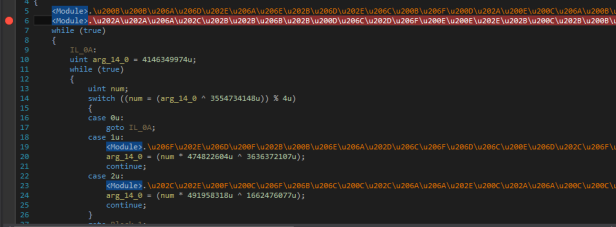
We have to delete proxy, which is that :
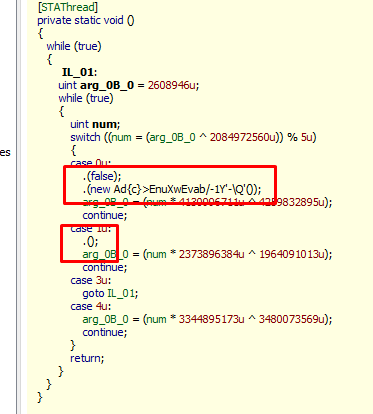
The real call is hidden. To decrypt that, we’ll use proxy deleter by Davicore : http://ge.tt/7wttili2 (don’t check remove Junk methods ! )
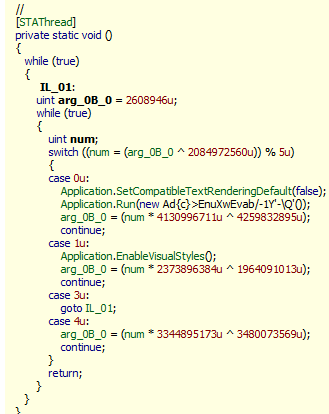
As we can see, proxy are deleted. Now, we can decrypt string using codecracker string decryptor : http://ge.tt/1Sd4jli2
Then, remove control flow using codecracker switch killer : http://ge.tt/2pO8jli2
Here’s how it looks like :
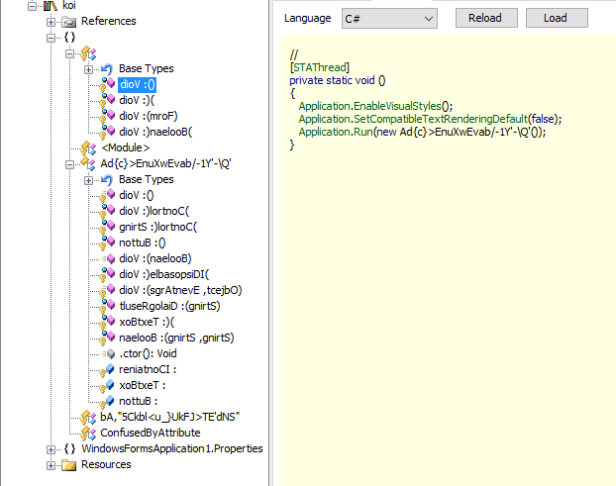
Finally, use de4dot for last fixes !
Enjoy 😀
For question : mindlockreverser@gmail.com or Skype : MindSystemm